8 Ways to Shore Up Your Charity’s Data




In today's digital world, your charity's data is an invaluable asset, underpinning supporter relationships, driving your mission, and ensuring your vital work continues. But it’s also a privilege to have, and people expect it to be kept safe. What happens when that data is compromised? Recent events in the sector, from the Advanced data breach, to the Blackbaud ransomware attack or the NHS Synnovis attack, and the resulting ICO fines, offer sobering but invaluable lessons for all charities. Robust data security isn't just a "nice to have," it's absolutely critical for safeguarding your mission, the people you serve, and your charity’s financial stability.
Before we go any further, we’re not here to fear-monger, nor are we here to point fingers at other technology companies. These are scary scenarios where highly sensitive data has been accessed by bad people, and figuring out how that could have been prevented is the best way to safeguard other charities from the same fate in the future.
Quick note: we do mention different security software below, but only as examples. We're not affiliated with any of them. Do your research to find out what works best for your charity.
A great way for charities to think about data security is in terms of layers. A strong password policy is an example of a layer of security, a keycard entry system to your office is another. However each layer of security will inevitably have flaws; a keycard can be left on the bus, a strong password can be accidentally shared in an email chain. The solution? Cheese, surprisingly.
The Swiss Cheese Model is a useful way to visualise cyber security systems. Every security mechanism is imperfect and will have some holes, much like a slice of Swiss cheese. The solution is to take a layered approach to security, placing several different slices on top of each other. Now it’s far less likely that the holes will all line up, and we have built a robust security system from imperfect slices.
Okay we’ve got the idea, but what layers of security should charities be adding to keep their data secure? We’ve included some easy-to-implement and relatively cheap ones below, split into three sections. These are by no means exhaustive, but should help you to set up a solid foundation upon which you can build.
When software companies find small vulnerabilities in their systems, they release updates to patch over them and close the holes. Having a simple policy in place that tells your people to update their software right away will help keep your systems secure. You can go a step further and use software like NinjaOne or Kandji that force your people’s machines to install the latest updates. Not updating software is one of the causes linked to the Advanced data breach, which resulted in the ICO issuing a £3 million fine.
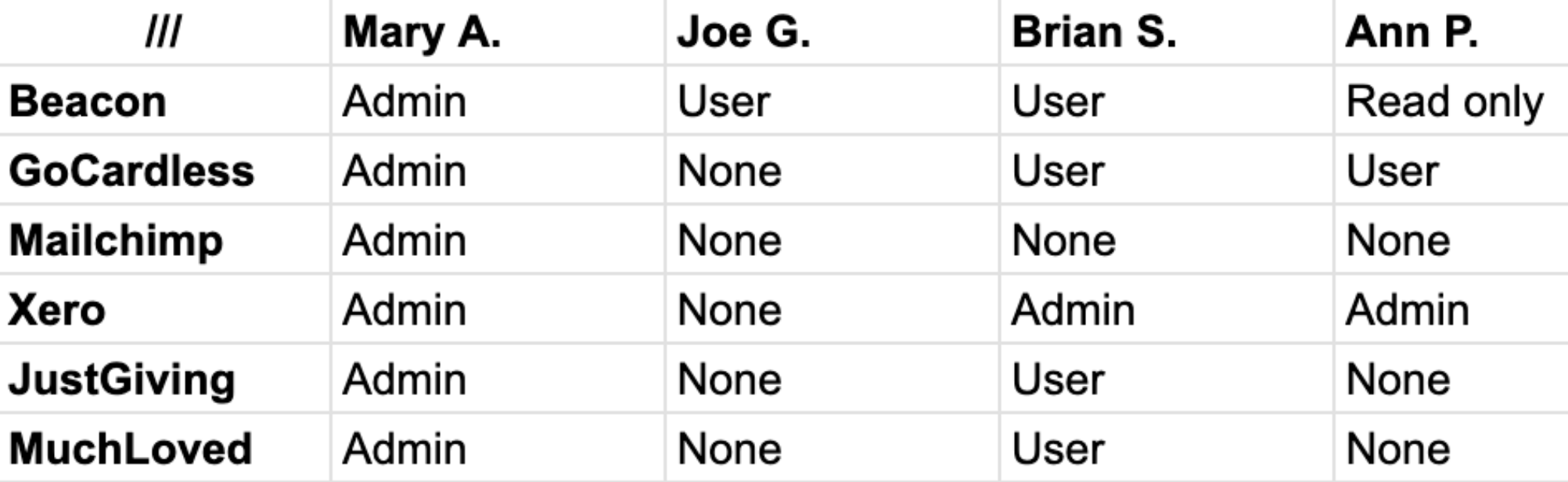
This can be a simple spreadsheet. On one axis, list all of the softwares your team uses. On the other, list your team members, then fill in the matrix with who has what level of access to each platform. We’ve done a simple example below. This is a great practice because it gives you a full overview of who has access to what.
Mistakes happen all the time, so make sure that people have access to everything they need to do their jobs, but nothing extra. You can go a step further and formalise the process where people must request access to new softwares, or formally ask to update their current access. We use a simple Beacon form for this, and the result is an live tracker of who has access to what at any given time.
They’re great for generating really strong passwords for all of your tools, and storing them all in one place, leaving you with just one password to remember in your head. On the topic of passwords, never share login details, even generic ones. And enable two factor authentication (2FA) everywhere. Everyone should have their own account for every platform you use. That way you’ve got another audit log of who made what changes when, and can spot suspicious activity, like if Dave from Finance is trying to log into your bank but he’s supposed to be on holiday.
2FA adds an extra layer of security, ensuring that the person logging in is who they say they are. Since the Advanced data breach, the ICO are on record having said that 2FA is “a fundamental security measure”. It’s no longer a “nice to have”. Password managers, like 1Password, are a cheap way to enforce these policies (around £15 per month), but if you really don’t have the budget for one right now, write up a simple password policy (more on policies shortly) that covers everything and make sure your team are aware of it.
A little more abstract, this is about creating a culture where your people feel comfortable to raise issues, safe in the knowledge that they won’t be reprimanded for doing the right thing. We’re all human, and humans make mistakes. Your culture is what will separate someone who panics and tries to fix a mistake themselves, often making it worse, from someone who follows procedure and reports it immediately. You can also create a Slack or Teams channel where your people feel comfortable posting anything security related.
There’s no such thing as a stupid question when it comes to security.
Don’t be afraid to have fun with this. At Beacon we’ve got a security mascot, the Security Llama (they’re famously good guard animals). Popped to the kitchen and left your laptop unlocked? That’s a no-no. And The Security Llama will be on your desk when you return, scolding you. It’s simple and playful, but encourages people to be security-aware, lest they be publicly shamed by a stuffed toy wearing children’s sunglasses.

Policies are the rulebook for how your organisation should operate and the processes that govern how things are done. If policies aren’t written down, they aren’t followed. And expect the same result if they’re needlessly long and complex. If you don’t have any right now, that’s fine - start small and build on them. At some point, something will probably go wrong, so make sure to write an explicit policy on “How to panic correctly”, and update your polices after any incidents to help avoid it happening again. If you have your policies written down already, great! Make sure your team can easily access them, and that they’re easy to understand, especially for new-starters.
A lot can change over the course of a year, make time to go through your policies regularly with your team. Include any changes that resulted from potential mistakes (no finger pointing, remember we want a positive culture of security!), examples of recent incidents that you can learn from, or new threats to look out for. You may feel like you’re not qualified to run a session like this, but any session is better than none at all. If you’d rather, you can work with a security consultant to fill the gap.
Top tip: if you want it to sink in, make it fun! Add jokes so the content is more engaging, bring snacks, do a quiz at the end and give out prizes. Death-by-powerpoint style meetings are not memorable. Here’s a cringeworthy (but memorable) line from our own security training: “Security, like onions and ogres, has layers” - one for the Shrek fans out there!
Okay I’ll admit that one is a mouthful - let’s unpack it a little. ISO 27001 (pronounced: eye-so twenty-seven thousand and one) is the most highly regarded global standard for data security systems. The most up-to-date version is the 2022 version (you’ll see it written as “ISO 27001:2022”).
The second thing you need to look out for is if the ISO certificate was issued by a UKAS accredited auditor. This means that the auditor who issued the certificate, is also certified themselves. If a provider is ISO 27001 certified, by a UKAS accredited auditor, you can be confident that they truly care about keeping your data safe, and they’ve done the work to show it. This is the kind of badge to look out for.

Remember our Access Matrix from earlier? Go through that list and check which providers are accredited and which aren't. If you find one that isn't, you have a decision to make - stick with them and accept a certain level of risk, or see what other options are out there. Do charities need to do ISO27001? You could do it, but it’s a lot of work. If you want to get certified, it might be more practical to start with Cyber Essentials before looking into something like ISO27001.
Question providers about their approach to data security and the features they’ve got to ensure that everything is kept safe, both on their side of the fence and on yours. How do you store back ups? Is our data encrypted at rest? Can I restrict which features, data, records or fields that different people can access? Can I have my team sign in with Google or Microsoft? Can I undo an import if it overwrites important data? Can I force all users to enable 2FA? Your data should have the safest home possible, so don’t be afraid to give providers both barrels here.
So we’ve delved into the importance of a layered approach to security, through llamas, ogres and cheese.
Remember, no system is 100% perfect. Your people will make mistakes, and malicious actors are always finding new ways to get into places they shouldn’t be, so your approach to security needs to be adaptive. Add new layers of protection, improve policies, keep your people updated, and encourage an open, judgement-free culture of security.
We hope this guide has shed some light on what can feel like a daunting topic.
If you’re looking for a safe home for your data, we’d be more than happy to help. Just book in a time to chat with a friendly member of the team.